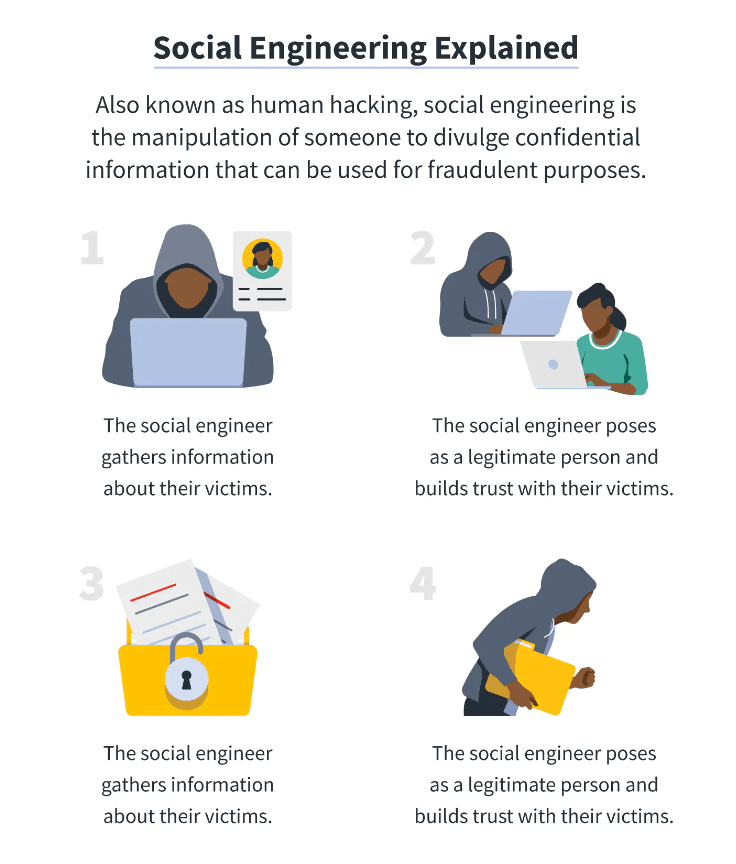
Social engineering is a technique used by hackers and cyber criminals to manipulate individuals into giving away sensitive information or performing an action that will compromise their security. This can take many forms, including phishing emails, phone scams, and fake websites. The goal of social engineering is to gain access to information or systems that would not otherwise be accessible to the attacker. In this blog post, we will explore what social engineering is, how it can affect you, and how you can protect yourself from it.
What is Social Engineering?
Social engineering is the art of manipulating people into performing actions or divulging confidential information. This technique is often used by hackers and cyber criminals to gain access to secure systems or sensitive data. Social engineering attacks can come in many different forms, such as phishing scams, pretexting, baiting, and tailgating.
Phishing scams are the most common form of social engineering attack. They typically come in the form of an email or text message that appears to be from a legitimate source, such as a bank or other financial institution. The message will often contain a link that takes the recipient to a fake website that looks identical to the legitimate site. The victim will then be prompted to enter their login credentials, which will be captured by the attacker.
Pretexting is another form of social engineering that involves creating a false pretext or scenario in order to gain the trust of the victim. For example, an attacker may pose as a vendor or supplier and request sensitive information from an employee. The attacker may use information obtained through pretexting to gain further access to the victim’s systems or accounts.
Baiting is a technique that involves enticing the victim with something of value in order to get them to perform an action that will compromise their security. For example, an attacker may leave a USB drive with a label indicating that it contains sensitive information. When the victim plugs in the USB drive, malware is installed on their system, giving the attacker access to their data.
Tailgating is a physical social engineering attack that involves following an authorized person into a secure area. For example, an attacker may wait outside a secured door and ask someone to hold the door open for them, claiming they forgot their access card. Once inside, the attacker can gain access to sensitive data or systems.
How can Social Engineering affect you?
Social engineering attacks can have a devastating effect on both individuals and organizations. In many cases, the attacker is able to gain access to sensitive information such as login credentials, personal information, and financial data. This information can then be used for a variety of purposes, such as identity theft, financial fraud, or corporate espionage. Social engineering attacks can also be used to spread malware and other types of malicious software, which can compromise the security of entire networks.
Protecting yourself from Social Engineering
There are several steps that you can take to protect yourself from social engineering attacks. Here are a few key strategies:
Be cautious of unsolicited emails or messages. If an email or message seems suspicious, do not click on any links or provide any personal information. Instead, contact the organization directly to confirm the legitimacy of the message.
Be wary of phone calls from unknown numbers. If someone claiming to be from a bank or other organization asks for personal information over the phone, do not provide it. Instead, hang up and contact the organization directly to verify the request.
Use strong passwords and two-factor authentication. Strong passwords are essential for protecting your accounts from unauthorized access. Two-factor authentication adds an extra layer of security by requiring a second form of authentication, such as a fingerprint or a one-time code sent to your phone.
Keep your software up-to-date. Software updates often include security patches that address known vulnerabilities. Keeping your software up-to-date can help prevent attackers from exploiting these vulnerabilities.
In conclusion, social engineering is a serious threat to our personal and professional security, and it is important to take the necessary precautions to protect ourselves from these attacks. By being aware of the different forms of social engineering, we can better recognize and avoid these attacks. It is also important to stay informed about the latest security threats and best practices for protecting ourselves online. By taking proactive steps to protect our personal and professional information, we can help ensure that we do not fall victim to social engineering attacks and maintain the security of our data and systems. Remember, it is always better to be cautious and verify the legitimacy of requests than to risk exposing ourselves to the dangers of social engineering.
I need more help.
If you need help with your company’s cybersecurity, we are here to help. Contact us for a Free IT Consultation. In the meantime, read about what others have said about our services.