What is Endpoint Detection and Response (EDR)?

In today’s digital landscape, cybersecurity threats are evolving and increasingly sophisticated. Traditional security measures like firewalls and antivirus software can no longer combat organizations’ threats. This is where Endpoint Detection and Response (EDR) comes into play. EDR has emerged as a critical component of modern cybersecurity strategies, providing organizations with the ability to detect, investigate, […]
Security Information and Event Management (SIEM)

In the ever-evolving cybersecurity landscape, businesses face many potential threats daily. Once hailed for convenience and efficiency, the digital realm presents a complex maze of vulnerabilities. In such an environment, robust security is imperative for safeguarding sensitive data and maintaining business continuity. Enter Security Information and Event Management (SIEM), a critical component in the arsenal […]
Securing Your Digital Perimeter

In today’s digitally interconnected world, where data breaches and cyber threats loom, safeguarding your network infrastructure is paramount. With the rise of cloud computing, traditional network security models are transforming towards more dynamic and scalable solutions. Cloud-based network security emerges as a formidable ally in this ongoing battle against cyber adversaries. Understanding Cloud-Based Network SecurityAs […]
3 Ways To Navigate the Terrain of Vulnerability Management and Assessment!

In today’s rapidly evolving digital landscape, vulnerability management and assessment have become critical pillars of cybersecurity strategy. With cyber threats proliferating and becoming increasingly sophisticated, organizations must adopt proactive approaches to identify, prioritize, and mitigate vulnerabilities in their systems and networks. This blog post delves into the intricacies of vulnerability management and assessment, exploring their […]
Boosting Security: 4 Ways to Safeguard Against Geopolitical Threat

Boosting Security: 4 ways to Safeguard Against Geopolitical Threats In an interconnected world where technology bridges continents and economies, the landscape of geopolitical threats has become increasingly complex and pervasive. From state-sponsored cyberattacks to economic warfare, the dangers posed by geopolitical tensions can have far-reaching consequences for businesses and individuals alike. Identifying these threats, understanding […]
Unlocking Seamless Access: JumpCloud’s Superhero Approach for Google Enterprise Users
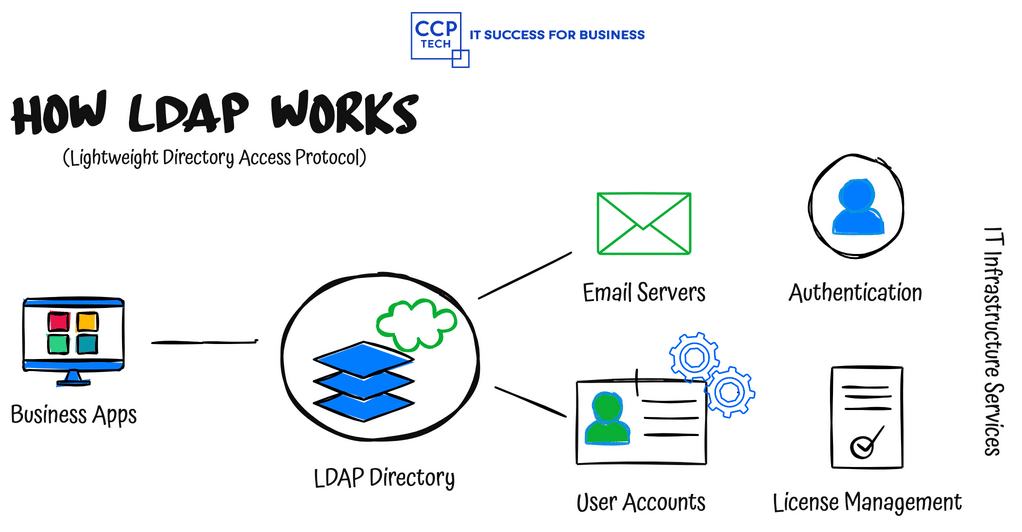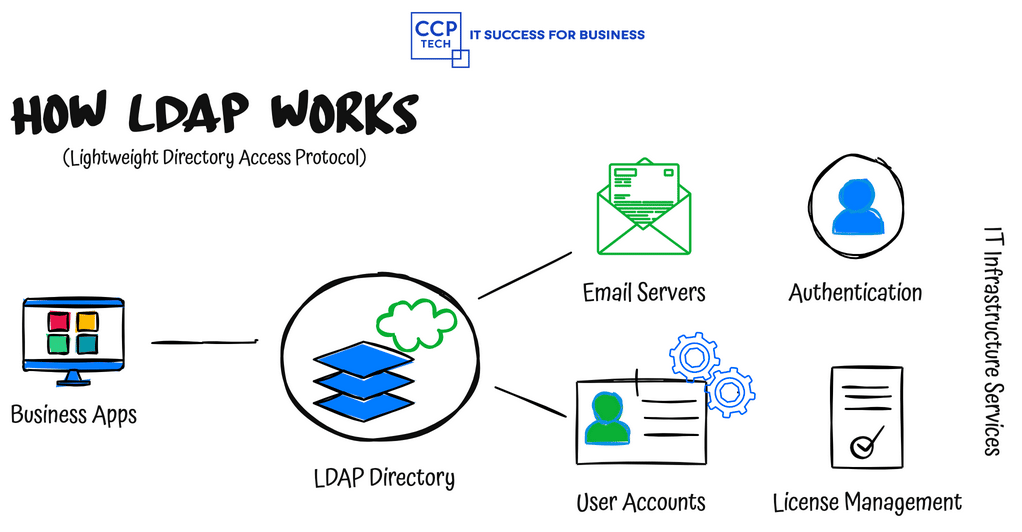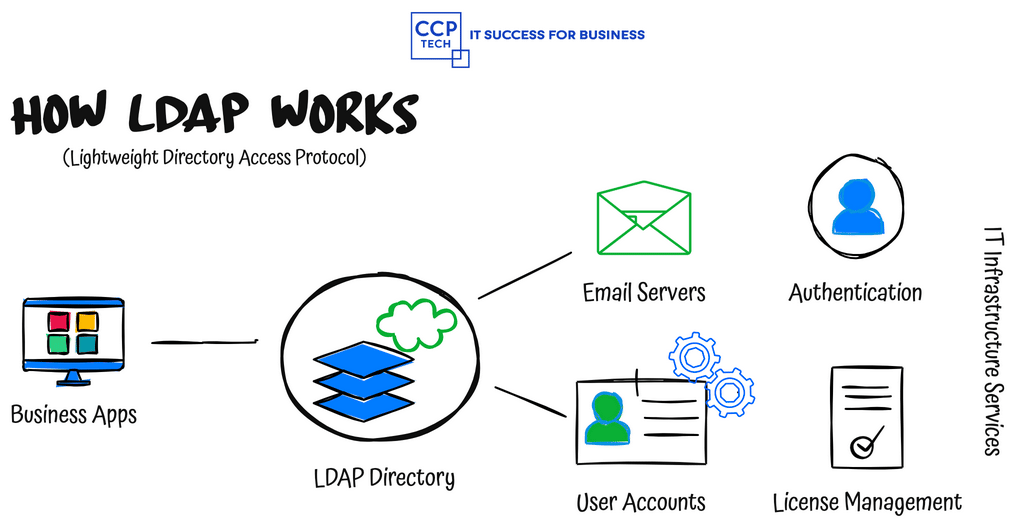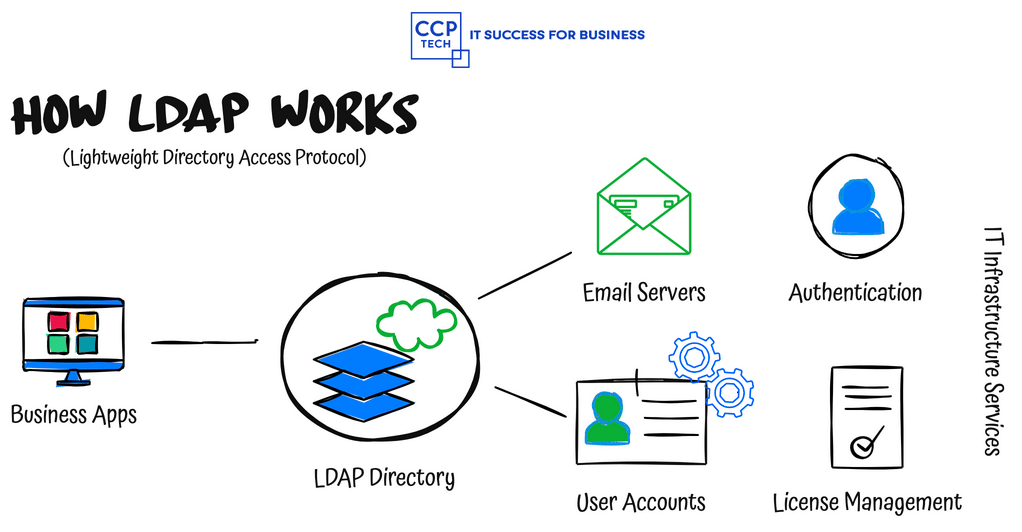
Unlocking Seamless Access: JumpCloud’s Superhero Approach for Google Enterprise Users In the vast digital landscape, the struggle to remember multiple usernames and passwords for various applications is a common frustration. But what if you could simplify your access with just one login? Enter Single Sign-On (SSO). This blog post delves into the magic of SSO, […]
4 Important Aspects of Dating Cybersecurity

In a world where technology is deeply ingrained in our daily lives, it’s no surprise that it has also transformed the landscape of romance. Dating in the digital age brings with it new opportunities, challenges, and considerations, much like the ever-evolving field of cybersecurity. In this blog post, we will explore the parallels between dating […]
Artificial Intelligence and Cybersecurity

In the rapidly evolving landscape of cyberspace, the symbiotic relationship between Artificial Intelligence (AI) and cybersecurity has become increasingly vital. As technology advances, so do the capabilities of both cyber attackers and defenders. This blog post explores the intersection of AI and cybersecurity, delving into how AI is transforming the way we protect our digital […]
Cybersecurity Awareness in 2024: Navigating the Evolving Threat Landscape

In the fast-paced digital age of 2024, where technology continues to advance at an unprecedented rate, the importance of cybersecurity awareness has never been more critical. As our reliance on digital platforms grows, so do the threats posed by cybercriminals. This blog post aims to shed light on the current state of cybersecurity and highlight […]
A Guide to Your IT Needs in 2024

As we usher in a new year, the ever-evolving landscape of technology continues to shape the way businesses operate. With rapid advancements and emerging trends, staying ahead of the curve in the realm of IT is crucial for success. In this blog post, we’ll explore key considerations and guide clients on how to address their […]
Cybersecurity Cleanse Into 2024

In an era dominated by technology, our reliance on digital platforms and interconnected systems has never been greater. With this increasing dependence comes the pressing need for robust cybersecurity measures to protect sensitive information from the ever-evolving threats that lurk in the digital realm. This blog post explores the concept of “cybersecurity cleansing” – a […]
User Errors in Cybersecurity

In an era dominated by digital interactions, the importance of cybersecurity cannot be overstated. Organizations invest heavily in advanced technologies, firewalls, and encryption to fortify their digital fortresses. However, a significant vulnerability often goes overlooked amidst these sophisticated defenses: user error. This blog aims to shed light on the role of user errors in cybersecurity […]
20 Gift Ideas for Technology-Loving People

It’s everyone’s favorite time of the year! No matter which holiday you celebrate, everyone needs good gift ideas for the ones we love. Sometimes, that can be a challenge for those who love technology. We’re here to give you ideas for some of our favorite picks. Smart Home Devices:Smart speakers (e.g., Amazon Echo, Google Home, […]
Cybersecurity During The Holidays

The festive season is a time for joy, giving, and, unfortunately, increased cyber threats. As we immerse ourselves in holiday cheer, cybercriminals are busy devising schemes to exploit the festivities for their gain. From online shopping to social gatherings, here’s your guide to staying safe and secure in cyberspace during this wonderful time of the […]
How IoT and Cybersecurity Transform Thanksgiving and Holiday Shopping

How IoT and Cybersecurity Transform Thanksgiving and Holiday Shopping As the festive season approaches, the integration of technology into our holiday traditions becomes more evident than ever. One area where the Internet of Things (IoT) is making a significant impact is in the realms of Thanksgiving celebrations and holiday shopping, all while emphasizing the importance […]

