Enhance Network Security with JumpCloud’s Zero Trust Approach
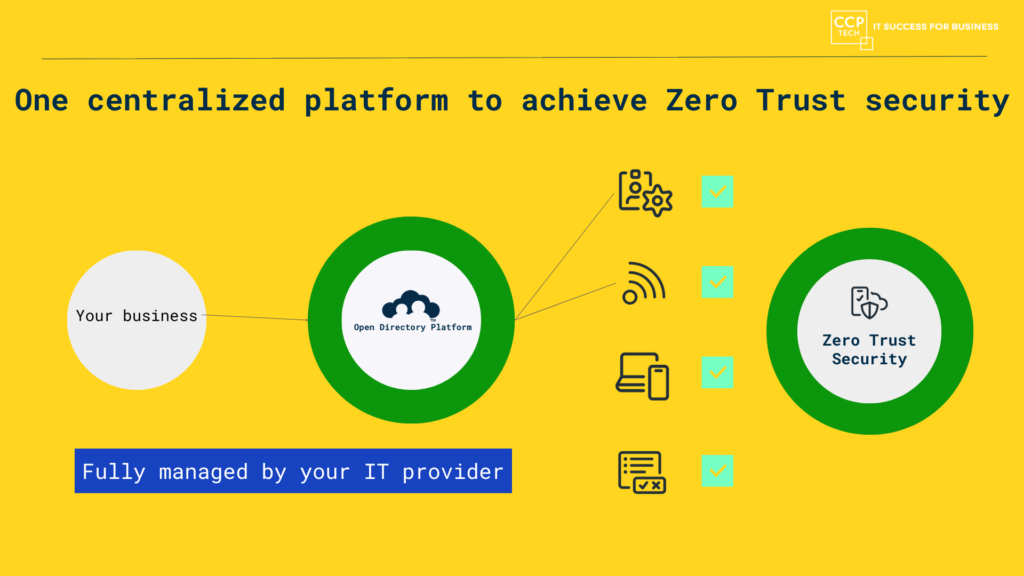
In today’s rapidly evolving digital landscape, cybersecurity threats continue to proliferate, posing significant challenges to organizations of all sizes. As traditional network perimeters dissolve and remote work becomes the new norm, ensuring robust security measures is paramount. One approach gaining traction in the cybersecurity realm is Zero Trust, a model that challenges the traditional security […]
Enhancing Automotive Dealership Efficiency and Security with JumpCloud
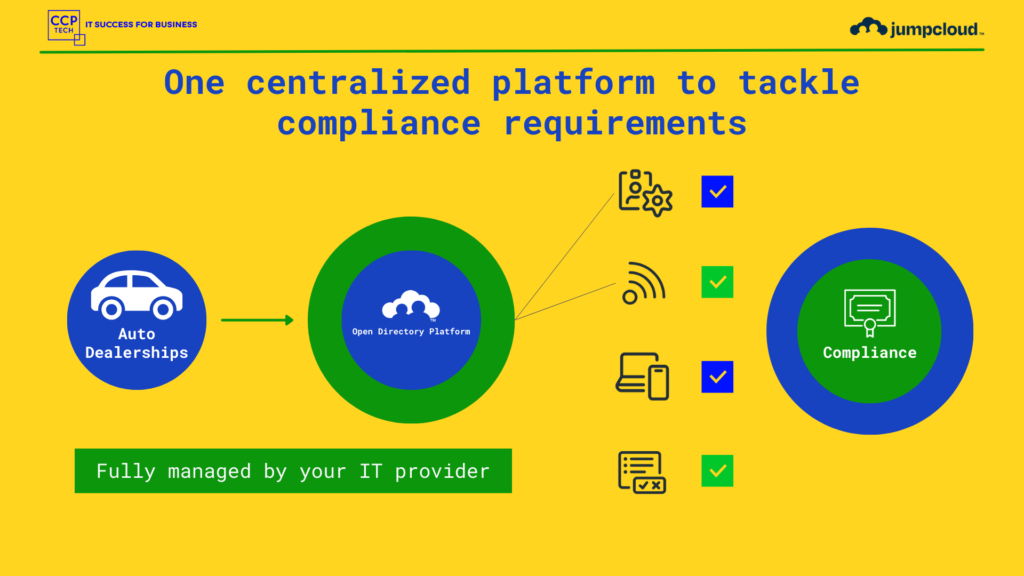
In the fast-paced and competitive automotive industry, dealerships are constantly seeking innovative solutions to streamline operations, enhance security, and improve overall efficiency. One such solution that has gained traction in recent years is JumpCloud. This cloud-based directory platform offers a comprehensive set of features that can significantly benefit automotive dealerships, from small family-owned businesses to […]
The Power of Multi-Factor Authentication with JumpCloud
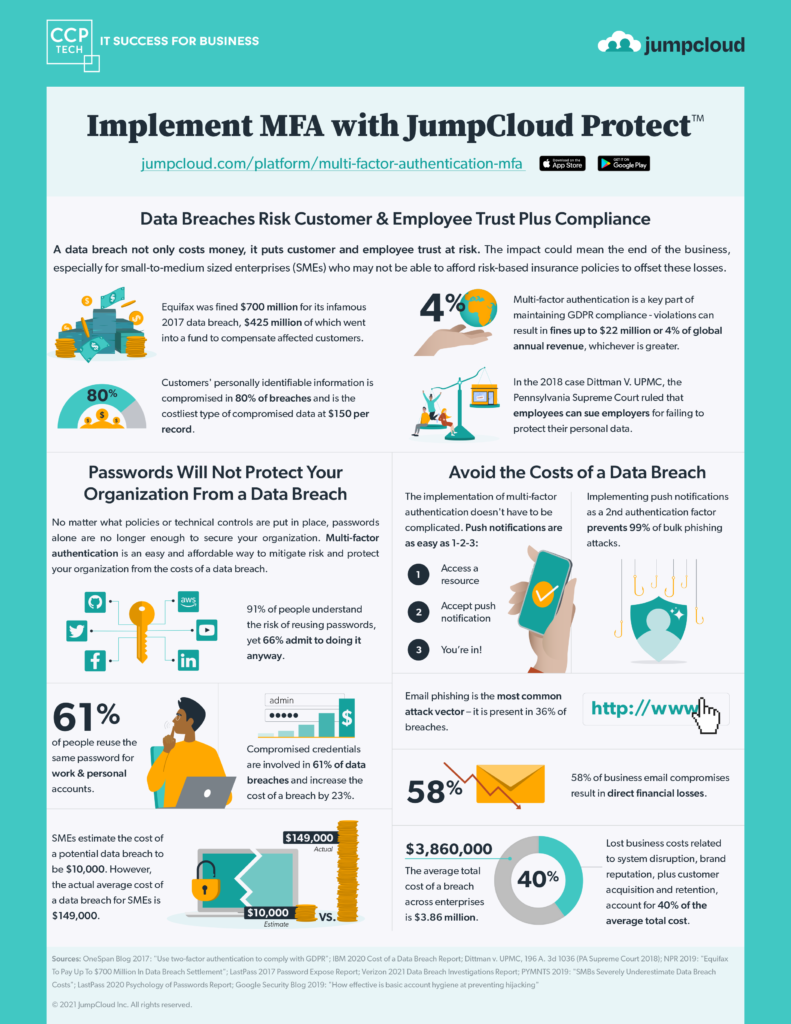
The Power of Multi-Factor Authentication with JumpCloud In today’s digitally-driven landscape, protecting sensitive information is paramount, given the average total cost of a breach across enterprises standing at a daunting $3.86 million. As 58% of business email compromises result in direct financial losses and email phishing remains the most common attack vector, organizations are turning […]
Revolutionizing Microsoft Office 365 Access with JumpCloud
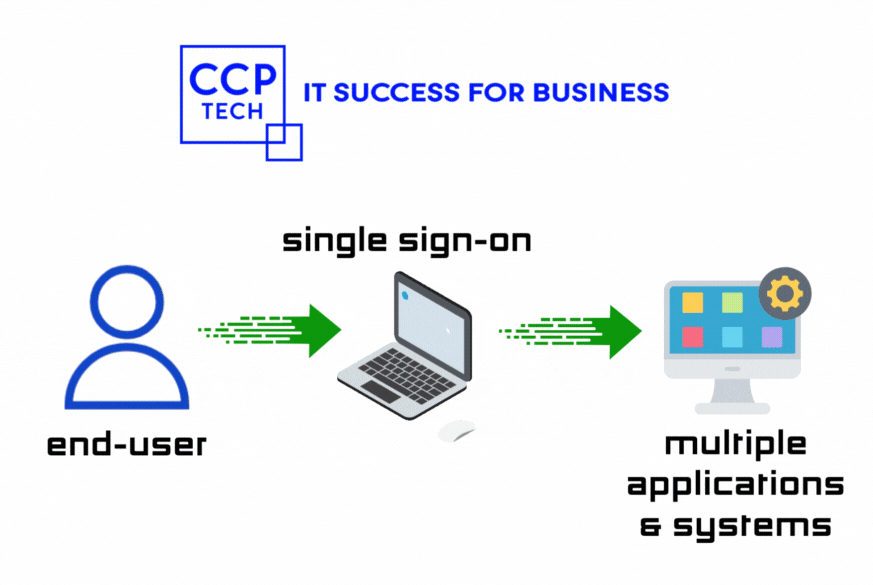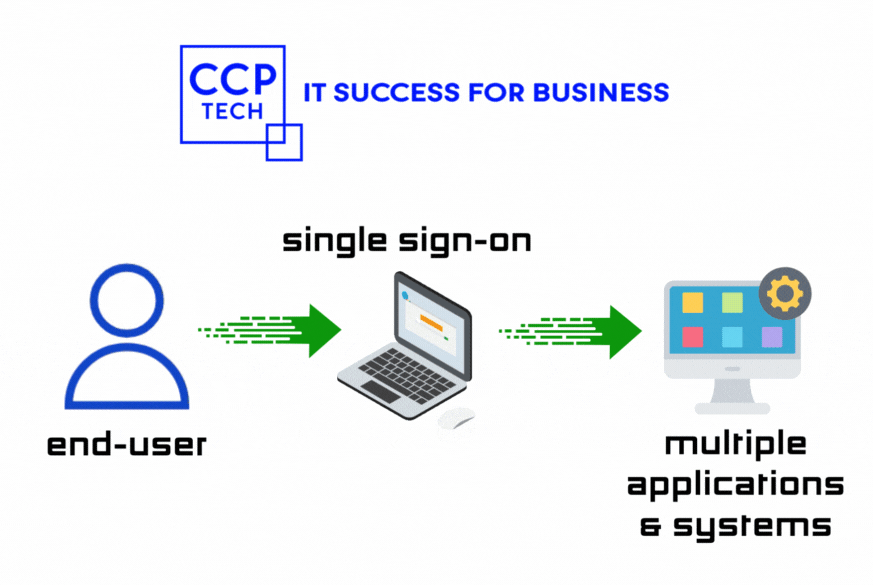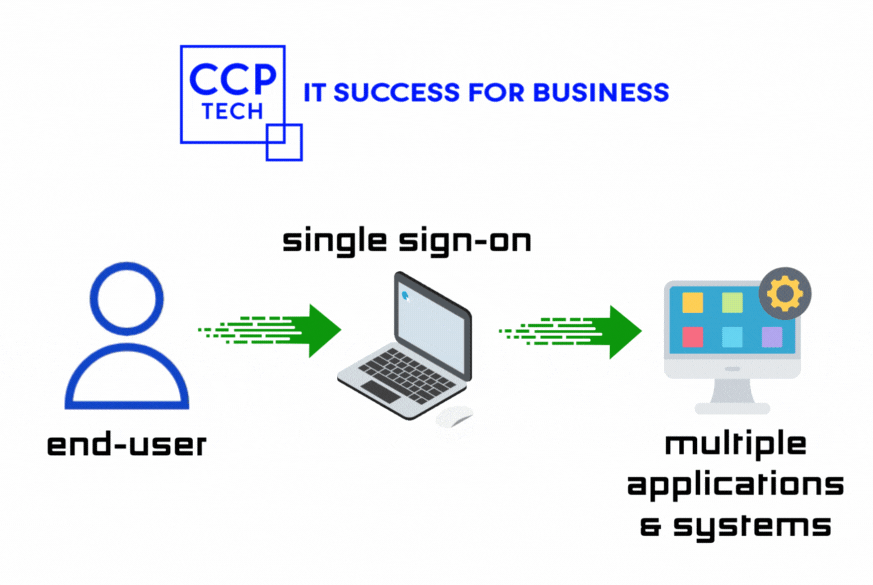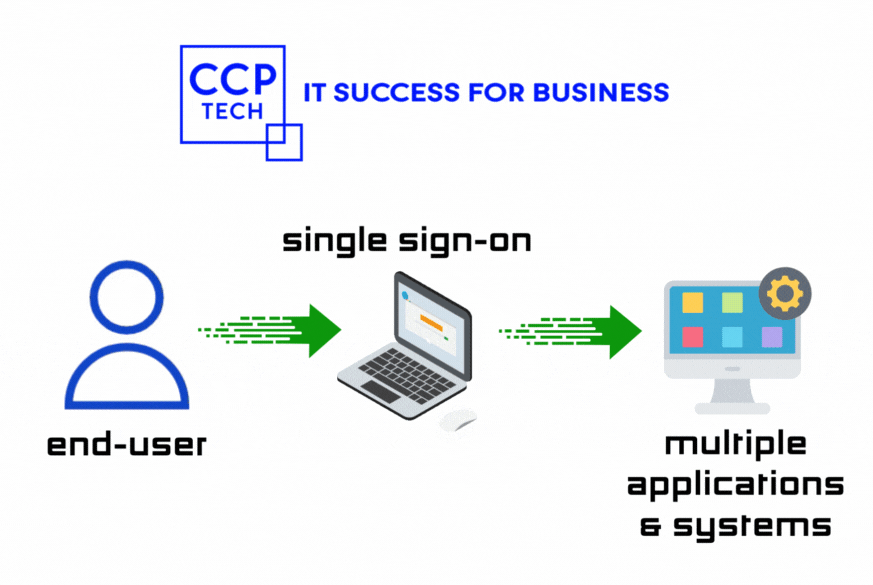
Do you ever find yourself drowning in a sea of passwords when trying to access various Microsoft Office 365 (O365) apps? Imagine a world where you only need to log in once to effortlessly access all your tools. Welcome to the realm of Single Sign-On (SSO), where JumpCloud emerges as your digital superhero, simplifying access […]
Safeguarding Independence Cybersecurity Considerations for SMBs
Safeguarding Independence Cybersecurity Considerations for SMBs on Independence Day Independence Day is a time when individuals and businesses come together to celebrate the spirit of freedom and independence. However, amidst the festivities, it’s crucial for small and medium-sized businesses (SMBs) to remain vigilant about cybersecurity. In an era of escalating cyber threats, protecting sensitive data, […]
Enhancing Small Business IT
Enhancing Small Business IT: How a Managed Service Provider Can Make a Difference In today’s digital age, small and medium-sized businesses (SMBs) face numerous IT challenges that can impact their operations and hinder growth. From cybersecurity threats to data management and infrastructure scalability, SMBs often struggle to keep up with the rapidly evolving technology landscape. […]
Demystifying Common Terms and Acronyms in IT and Cybersecurity
Demystifying Common Terms and Acronyms in IT and Cybersecurity: Navigating the Path to Success with CCP Technologies Introduction: In the ever-evolving world of information technology (IT) and cybersecurity, staying updated with the latest terms and acronyms is crucial. This blog post aims to shed light on some common jargon and acronyms used in these fields. […]
Navigating the Challenges of Hybrid Workforce Management
Navigating the Challenges of Hybrid Workforce Management and Security Concerns with BYOD Introduction: The rise of hybrid work environments, where employees split their time between remote and office work, has brought forth numerous benefits for businesses. However, it has also introduced new challenges, particularly in terms of workforce management and security concerns. One area that […]
Zero Threat Security – Strengthening SMBs
Zero Threat Security – Strengthening SMBsIn the ever-evolving landscape of cybersecurity, the concept of Zero Threat Security has emerged as a powerful approach to safeguarding small and medium businesses (SMBs). This proactive strategy aims to eliminate potential threats before they can cause any harm. In this blog post, we will explore what Zero Threat Security […]
Security Hygiene and Posture Management
In today’s technology-driven world, security hygiene and posture management have become essential for businesses to keep their sensitive data and information safe from cyber threats. In simple terms, security hygiene refers to the practices and measures taken by organizations to ensure their network, systems, and applications are secure from potential vulnerabilities and attacks. Posture management, […]
What is going on with my email?
What is going on with my e-mail?As the threat landscape continues to evolve and security organizations struggle to update their posture to keep clients protected, large entities like Microsoft often make seemingly minor adjustments which have big impacts at scale. For the past 2 years now, Microsoft has adopted a practice of security baselining where […]
Social Engineering and Phishing
Social engineering and phishing attacks are still widely used by cybercriminals to gain access to sensitive information and systems. These attacks can have devastating consequences for businesses, including financial losses, reputational damage, and legal action. In this blog post, we will discuss the latest techniques used in social engineering and phishing attacks, how business owners […]
Artificial intelligence (AI) and Cybersecurity
In today’s interconnected world, cybersecurity has become a critical issue. As businesses and individuals rely more on technology to manage their affairs, the risks of cyber attacks have increased. Fortunately, artificial intelligence (AI) has emerged as a powerful tool in the fight against cybercrime. In this blog post, we will explore how AI is being […]
Cloud Security
The use of cloud computing has grown significantly in recent years as more and more companies migrate their data to the cloud. This shift has brought many benefits such as cost savings, scalability, and flexibility, but it has also brought new security concerns. With sensitive data being stored on third-party servers, cloud security has become […]
Internet of Things (IoT) Security
The Internet of Things (IoT) has revolutionized the way we interact with our devices. Smart devices have become an integral part of our lives, from smart thermostats that regulate our homes’ temperature to smartwatches that track our fitness goals. However, as IoT devices continue to proliferate, so do the security risks associated with them. The […]

